-
Posts
18,764 -
Joined
-
Last visited
-
Days Won
735
Everything posted by wolstech
-
Krydos can do this for you.
-

[Solved] Suspended: intraserverin
wolstech replied to intraserverin's topic in Suspended and Queued Accounts
For now you have to ask us and we'll post the usage chart for you if you want to see it, but eventually you'll be able to see it in the dashboard at https://heliohost.org/dashboard/load/ Unsuspended. -

[Solved] Suspended: intraserverin
wolstech replied to intraserverin's topic in Suspended and Queued Accounts
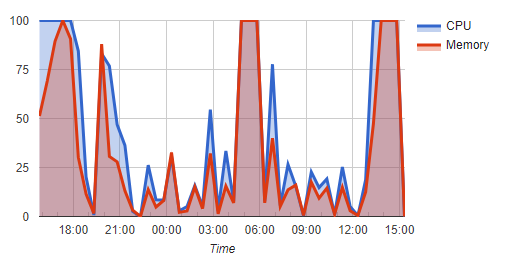
You caused a significant amount of load and brought the server to a crawl for 3000+ other websites...your CPU usage was more than twice that of the second heaviest account. This was your load over the past 24 hours...during those big spikes, each which lasted an hour or more, your account was slamming the CPU and the memory usage wasn't much better (that cliff at the end is where I suspended you and your load went to 0, which brought the server back to a tolerable overall load). Some software products are especially bad about this, Wordpress (especially with plugins) being the most common offender. Other software like Moodle, Magento, and Prestashop are also common causes. How do you plan to fix this? -
Added. It'll take up to 2 hours to work. Please make sure DNS has an A record pointed to 65.19.141.77 and AAAA pointed to 2001:470:1:1ee::2002.
-
Invite sent.
-
A donation would be a Tommy account yes. Do you have the transaction ID from that donation? If you have that I can cancel the Johnny invite for you and replace it with a Tommy account with 4000MB storage.
-
Yeah sometimes these just take a little while. Glad to see its working
-

[Solved] please add this domain in my account.
wolstech replied to intraserverin's topic in Customer Service
Added. Please make sure the DNS is set up and has A records pointed to 65.19.141.77. It'll take up to 2 hours to work. -
This guy crashed the database servers: https://helionet.org/index/topic/56331-krydos-suspended-michaelwschmidt/ Krydos suspended him and it's working again.
-

[Solved] Suspended: michaelwschmidt
wolstech replied to michaelwschmidt's topic in Escalated Requests
Crashed PostgreSQL crashed MySQL and over 11 GB storage used. You crashed the server and caused downtime for 3000+ other websites, and were over quota by nearly double. A 20GB database will not fit even on the largest Tommy account (which has a disk space limit of only 6000MB). You're well into VPS territory with a 20GB database. I'll let Krydos decide if he wants to unsuspend you... -
OK, I did some digging and this is weird. I see nothing in any logs about this account (hence the PM response I sent you), but you're right in that the address does work on the ETA page! Usually the accounts will show in the historical logs (I can usually see when it was created, etc.). Maybe the account was old enough to predate the logging for new accounts? Either way, I've sent an invite to the address on your forum profile since that old address looks to no longer be valid. Since there is no account to transfer I'm assuming this was on Johnny (Johnny users are being reinvited since we had to delete them when the server got hacked and they were all turned into phishing sites). The invite will most likely be in your spam folder since you use gmail. If so, please "Not spam" the invite so you receive future email from us.
-
Added. It'll take up to 2 hours to work. Please make sure you have your name servers pointed to ns1.heliohost.org and ns2.heliohost.org, or that external DNS has an A record pointed to 65.19.141.77 and an AAAA pointed to 2001:470:1:1ee::2002
-
Uncheck the box for wildcard certificate and try again. We don't support wildcard certificates on our subdomains or on any other domain that uses our name servers (your own domain + external DNS can do it if you manually create the records, but that doesn't apply here since you're trying to use a .helioho.st domain).
-

Help with Thirty Bees/Prestashop installation
wolstech replied to mothzee's topic in Customer Service
Without seeing the errors we can't really help. Also, none of us have any real experience with these two programs which is why you're not getting an answer. The most we can do is look at the errors and troubleshoot based on that. I can say that prestashop specifically has a history of getting people suspended for load though. Can you please post the errors your experiencing and how to reproduce them? -
VPSes don't count as a second account, you're fine to have 1 shared hosting account and 1 VPS (in fact, you can have more than 1 VPS too, we have customers with 2 of those). Do you still want your account removed?
-

[Solved] Questions about Addon/Parked Domains and Document Root
wolstech replied to sagnik's topic in Escalated Requests
Which ones need their docroot moved? We can move them for you, but keep in mind that if your scripts care about the name of a docroot, they're poorly written. Good scripts won't care where they are located. You should be using relative paths to reference files within a website, and if multiple sites are doing something like sharing includes, you'd be best served by moving the shared files outside of the docroot of another website (e.g. instead of a script for one domain needing a shared include referenced as ../../otherdomain.heliohost.us/public_html/includes/something.php, move the folder containing the shared components into your home folder and edit the sites using them to reference it as ../../includes/something.php). -
What is your old account's username (or the email address it was under)? The info on your forum profile doesn't match any accounts I can find.
-

[Solved] Questions about Addon/Parked Domains and Document Root
wolstech replied to sagnik's topic in Escalated Requests
They don't fit in your account, so no. If we removed 2 and added those 4, you'd have 12 domains, which is over the limit of 10. Also, plesk uses httpdocs instead, it is equivalent to public_html. The sgads domain does not work for me, it resolves to a suspended page for a cpanel server. If it's working for you, it's probably something like being in the host file on your computer. -
Krydos will need to do this as I don't know how to create the wildcard domain on the DNS side. EDIT: Also, be aware that we do not support wildcard SSL certificates when using our DNS, so the wildcard subdomain will not be able to receive an SSL certificate.
-
Surprisingly enough, not everyone is. About 15% of our total active accounts are still on Ricky despite it having had no control panel for 2 years...not as low as most would expect. That said, I suspect many of them are abandoned at this point. Inactivity suspensions on Ricky stopped when cPanel died. If it goes like cPanel Tommy did, the accounts are likely going to be backed up and deleted if not moved by Sunday. All of them have been invited to move and either missed or ignored their invite.
-
That IP isn't blocked, which is kind of expected since the tommy2 link works for you. Not sure why you were having trouble with the dashboard but glad to see you're able to get into your account Please let us know if you need anything else.
-
It was because Apache was disabled for that subdomain (there's an option to make a domain nginx only). If Apache is disabled for a domain, the only supported PHP version is 8.2.7. I'm not sure if you can see that option or not, but if you can, for reference you select the domain, then: Hosting & DNS tab->Apache & Nginx->checkbox labeled "Proxy Mode"->Apply. I turned Apache back on for this subdomain and set the PHP version to 8.0 for you. The changes will take up to 2 hours to take effect.
-
A timeout is usually a firewall block, but I'm not seeing the IP on your post listed in the firewall as blocked. Are you posting from the same IP that has the issue? If not, what IP is impacted (you can check by visiting this page from the computer that doesn't work: https://heliohost.org/ip.php and telling us the IP it shows you)? Also, if you visit tommy directly do you see a Plesk login ( https://tommy2.heliohost.org/ )?
-
Deleted.
-

[Solved] still having issues getting into plesk
wolstech replied to sunamong's topic in Customer Service
See my response here: https://helionet.org/index/topic/56300-solved-i-think-my-ip-blocked/